Introduction
About eight years ago I wrote an
optimistic article on the topic of spam that has been widely linked and copied. During the intervening decade the original article's content grew increasingly dated and irrelevant, so I decided it's time for a new description of the spam problem. This page is the result.
Expressed very simply, spammers have colluded with corrupt and/or stupid politicians to create special-interest laws that legitimize their crimes, have attacked their opponents using direct technical attack methods to silence them, or have employed expensive, frivolous legal proceedings only spammers can afford to drive their opponents out of business. Spammers have morphed into a cybernetic Mafia, an international criminal organism for which no act is too vile or low.
Spammers began as a minor annoyance, but they now control the Internet. Any critic that becomes sufficiently threatening is systematically attacked by an international network of zombie computers able to remove dissenting voices and activities from the Internet. Anyone who claims that a particular named party is a spammer is likely to be sued until he can no longer bear the legal burden, regardless of the truth of his claims.
In most countries, the majority of e-mail traffic consists of spam, and the numbers get worse by the day. In practical terms, that means legitimate users of the Internet are now visitors, tourists, whose presence is tolerated by the real owners of the Internet — spammers.
Every cynical cliché about participatory democracy has had its turn on the stage in the struggle against spam — corrupt, misguided lawmakers and courts of law, examples of outright cowardice, free, open network protocols subverted and abused, and a gradual shift toward rule by the most parasitic and persistent, such that the rats are now in charge of the ship.
Some readers may wonder if the spam situation is really as bleak as I am painting it. After all, for most issues there is some basis for hope, some reason to say "the end is in sight." And in fact, about the spam issue, I can honestly say the end is in sight. According to statistics gathered by Ironport, a spam filtering firm, at the time of writing (late 2006),
nine out of ten e-mails is spam. All the spammers have to do is figure out how to exterminate that last ten percent, and the promised end will be reached —
all e-mails will be spam, all the time, day and night, 24/7.
And that's the good news. Read on for the details.
Some History
Figure 1: Original spam topology
Some younger Internet users may not realize the net wasn't originally meant to be the fantastically efficient advertising delivery vehicle that it is today. This is because the original Internet was used almost exclusively by academics and computer scientists — people who either didn't know about marketing or didn't care — to transmit technical information back and forth.
Before the invention of what we know as the WWW, the World Wide Web, people communicated using a handful of comparatively simple protocols like FTP (File Transfer Protocol), Usenet (a way to post and read messages in a plain-text public discussion board), and e-mail, originally a point-to-point communication protocol sort of like the conventional post office.
Most of these protocols predated the appearance of computers with graphic interfaces. Until about 1980 virtually all computer activities were carried out using text displays, typically 24 lines each of 80 characters (and a bit earlier, all computer entry and display appeared on paper, not glass).
This means that the present e-mail protocol, the way of handling e-mail, was created at a time when there was little point in defending against attack — after all, who would attack, and what would they gain? But around 1994, attracted like moths to a candle, the first spammers realized they could send an e-mail to each of a long list of trusting souls who placed their e-mail addresses on public display.
In the first phase of spam defense, operators of servers and individuals blocked e-mails by automatically reading the content of the messages or noting their origin (name or address). Some of these methods are still in use today, but with rapidly decreasing effectiveness.
Because of the open nature of the e-mail protocol, a malicious person can create an e-mail message that is not what it appears to be. It is possible to fake the source of the message, the sender, the return address, the IP (Internet address) of origin, and such additional trivial deceptions as a misleading subject line. It was at that point that I wrote my original anti-spam article,
archived here.
As the volume of spam increased, people became increasingly annoyed and some legal actions resulted, with much thrashing but little effect. The original delivery scheme consisted of a central spam server with a fixed IP that could not be disguised (see Figure 1), so filtering methods began to rely on lists of addresses known to be sources of spam. This could be called the vulnerable era — the spammers could emit spam, but they could not hide its origin.
Then two groups of unhappy Internet users chanced to meet. One group were the spammers, greedy, morally flexible individuals who had money but no technical skill. The other group were hackers (in the negative sense of that word) — mostly young, dispossessed teenagers with lots of technical skill but no money.
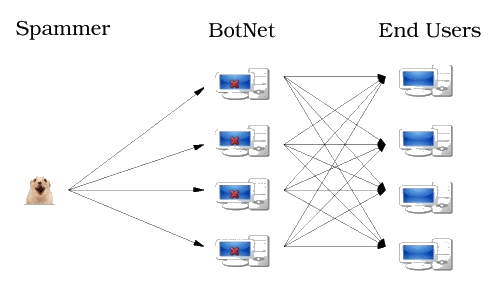
Figure 2: Current spam topology
The spammers wanted to get around the obstacles placed in their path by the server operators, who would quickly notice where the spam was coming from and either take action to shut it down at its source or automatically block a list of known spammer addresses. But the spammers had no idea how to avoid these methods. To the spammers, the Internet was just another dodge, a scam, like cure-everything magic magnets, miracle weight loss programs or underwater Florida real estate. The only difference was the Internet proved too complicated for a person armed with the education and ingenuity of a door-to-door encyclopedia salesman.
A typical young hacker of the era desperately needed money in order to buy a red sports car and impress a girl. To those with more life experience, such a project has two disastrous outcomes: the one in which you are rejected by the girl, and the one in which you are accepted by the girl. To be rejected means you wasted a lot of money on the kind of car known to attract policemen. To be accepted means you become responsible for someone so shallow as to be impressed by a red sports car. But digressions aside, our young hacker needed money.
Until this point in our story the spammers, virtual vagabonds, would wander about, hoping to find a server operator willing to host them, only to be thrown off one server after another. On the other side, sociopathic young hackers would code pathogens of dubious virulence, hoping to bring the Internet to its knees and become famous. Maybe this will work better than a red sports car.
Eventually, in a marriage made in hell, the spammers and hackers met and found common purpose. The spammers realized they could evade the handicap of having a recognizable source address by distributing the spam emission task among thousands, and eventually hundreds of thousands, of compromised computers running Windows (see Figure 2). The hackers found it relatively easy to infect lots of computers and turn them into mini-spam-servers. So there it is — the spammers are back in business, and the hackers can afford a red sports car.
All humor aside, this is an historical turning point. It is the point at which control of the Internet has begun to slip into the hands of criminals.
The Windows Problem
Microsoft Windows is by general agreement the worst operating system presently available. According to insider accounts, it is written by a loose gaggle of undisciplined "cowboy coders" whose individual contributions are knit together into an incoherent whole, rather than being made part of a coordinated, internally consistent, large software project, such as one reads about in computer science textbooks.
At the time of writing, even Microsoft's advocates have come to realize that Windows is out of control and cannot be meaningfully improved or added to any longer — it is now too complex and disorganized to admit incremental improvements. As to Vista, the current Windows version coming to completion at the time of writing, Microsoft management was obliged to face reality and, one by one, abandon the primary goals of the project, because the software base is now too complex and disorganized, and the working style of the programmers is not disciplined enough (more on these issues
here).
Because of the near-universality and poor quality of Windows code, Windows machines have become a favorite target of hackers. It is relatively easy to break into a Windows machine, plant some parasitic software, and turn the machine into a slave, a "bot". If the machine happens to be connected to a high-speed Internet connection, it is in an ideal position to do the bidding of criminals, 24 hours per day, often without any hint to the owner that it has been taken over.
It is only fair to add that the other commonly available operating systems (Mac OS X and Linux) are probably equally vulnerable to attack, and the only reason there are not more attacks on those machines is because they are few in number — hackers don't waste their time coding for machines that only represent a few percent of the total PC market.
It is estimated that several hundred thousand Windows machines are infected at the time of writing, each serving as a cell, a "bot" in a "botnet", a network of slave machines waiting to do the bidding of criminals.
Computer Pathogens
Computer software pathogens come in several varieties — viruses, worms and Trojans, to name a few. A virus, so defined because like its biological counterpart it attaches itself to, and depends on, a living organism (a computer program) for support, tries to insinuate itself into a computer, replicates there by attaching itself to as many programs as possible, and optionally propagates across any available network connection to other machines.
Worms behave much as viruses do, with the distinction that a worm is self-sufficient — it doesn't need to attach itself to a program, because it is a program. A "Trojan horse" or "Trojan" differs from a worm in that it arrives in disguised form, as part of a legitimate program or group of programs, and tries to remain undetected.
These pathogens have several purposes. One purpose might be to record the computer owner's keystrokes (this is called a "keylogger") and send them to a remote location for exploitation. A keylogger is a very high security threat, because the owner may enter sensitive personal information as bank account data and social security number, all forwarded to a criminal. Some people have the idea that, if a Web browser shows that it is visiting a secure Web site (signified by the appearance of a padlock) that what one types is therefore secure. But if a computer has been infected with a keylogger, all personal information must be assumed to be compromised, regardless of the nature of the transaction.
Another purpose for infecting a machine is to turn it into a spam server, a "bot" in a "botnet". In this case, the pathogen awaits instructions from a central control point (often an IRC posting is used to instruct the bot cells), and then acts in concert with many other machines according to the broadcast instructions.
One purpose for a botnet is to deliver spam in a way that is impossible to control (because each bot in the botnet has a separate address, so address filtering fails). Another purpose is to take part in a DDOS — a Distributed Denial of Service attack. A DDOS attack is a concerted effort to overwhelm a server with malformed packets, packets that have no legitimate purpose, that have been crafted to use up as much server time as possible. A concerted DDOS attack can absorb a server's entire capacity and make it invisible to its legitimate users — for the duration of the attack, the server might as well not exist.
DDOS attacks are sometimes carried out as part of a ransom scheme — "pay up or we'll keep you off the Internet" — or to try to silence critical voices, or to punish enemies of the "bot-herder", the controller of the botnet. Because a DDOS attack arrives from independent servers (and addresses) all over the world, and not unlike the spam scheme described above, it is not possible to control by address filtering. It is this sort of activity — cheap threats and big rewards — that attracts the attention of criminals, and that makes the Internet a haven for gangsters.
A closer look at spam
Spam has some things in common with other human activities and transactions. There is a sender and a receiver, each with different preferences and priorities. The sender hopes to use the spam as an advertisement for goods and services, and as with all advertising projects, there is a cost and a return. If no recipients ever responded to spam, it would die out in a fortnight — but there is always someone, brain-damaged or pathological, who responds to spam advertising. And the unit cost for spam is very low, so low that one can send out 100,000 spam messages, get only a few responses, and still make a profit.
One way to fight spam is to raise the unit cost per spam message. But since the advent of botnets, unit cost has gone down. Before botnets, spammers had to pay a server operator for the direct costs for the bandwidth used by the spam traffic, as well as some legal costs incurred by operating an illegal enterprise out of a legal server. This means a botnet — a
sub rosa network constructed out of many poorly defended home computers, without the knowledge of the computers' owners — can solve both the legal and unit cost problems. There are no ongoing unit costs if the spammer owns the botnet, and only small costs to create the botnet in the first place, and because the spammer's identity is concealed along with the botnet, the legal issue is moot.
Now for the recipient of spam. Spam blocking and filtering has had a short, depressing history. At first, spammers used normal, centralized servers, so it was a simple matter to block all packets arriving from that server. Sometimes a spammer would acquire an account under false pretenses and commence spamming, which might cause all traffic from that server to be blocked, which would hasten the spammer's departure. Sometimes a spammer would sign up for a 30-day free trial subscription at a large end-user service like AOL, using a false name, address, and credit card number if required, and spam until the account was shut down. Companies like AOL quickly realized what was going on and closed this loophole.
Spam filtering relies on methods that examine the e-mail header information, the subject line, and the content. Unfortunately, all of these can be faked. There was until recently some hope that by examining the message body, a spam filter could detect "organ enlargement" and similar terms and filter on that basis. The spammers have solved this problem by putting a graphic image where the text used to be. Images are more difficult and costly for a machine to convert into readable form, there is a lot of spam traffic, consequently this class of spam goes unexamined.
The summary of this issue from the recipient's perspective is that modern spam messages don't have to betray themselves by way of origin, return address, subject line, or message body. Put simply and directly, it is
impossible to use filtering methods to stop spam. Any filtering methods, any established criteria, will be adapted to by the spammers.
There is a filtering scheme that relies on validation. It works like this: on receiving a message, an e-mail program automatically sends out a validation post to the message's return address. The idea is that the sender has to reply to the validating post in order for the original message to be delivered to its recipient. The flaws in this scheme are so numerous that it can only be adopted by one of two classes of Internet user — persons "of diminished intellectual capacity" and
narcissists. The first group would not be able to think through what would happen if two validating-account people tried to contact each other:
- Person A posts a message to person B.
- Person B's e-mail program automatically sends a validating message to person A.
- On receipt of B's validating message, A's program sends a validating message to validate B's validating message.
- On receipt of B's message to validate A's validating message ... ad infinitum.
Someone will undoubtedly reply, "Oh, these validating programs solve the infinite-loop problem by automatically accepting a validating message without challenge." At which point I would say that the spammers now send out messages that look just like validating messages, thus destroying the entire method.
This validating scheme, with the glaring defect diagrammed above, is perfect for narcissists, because after all, they are the only important person on the planet. True to their status as narcissists, they won't consider the possibility that someone else might adopt the same strategy, because no one else really exists, or if they have the temerity to exist, they don't count (read more on narcissists
here). Actually, now that I think about it, adopting this validating scheme is as clear an indicator of clinical narcissism as owning a leaf blower (you know — instead of raking your own leaves, just blow them into your neighbor's yard. After all, he isn't a real person, he won't mind the leaves).
Now we turn to what is advertised in spam. Typically it is something no one would pay to have advertised, or it is something so obviously worthless or illegal that normal advertising channels are closed. The problem with advertising something illegal is that, in order for the message to serve any purpose, it must reveal the vendor's identity and contact information. This problem is often circumvented by locating the vendor in a country willing to tolerate anything.
There has been a recent surge in penny-stock scams, a practice known as "pump and dump". The perpetrator acquires a position in some worthless stock, then advertises the stock in a spam mass mailing, then, when the stock price has peaked, sells his position. This kind of scheme relies on a level of public stupidity that is a bit difficult to imagine, but, since it works over and over again, it must be true — people really do receive spam e-mails and then rush out to buy the stocks they advertise.
Then there are "phishing" spam mails. These pretend to be legitimate contacts from banks or credit institutions asking for validation of account numbers, passwords, and social security numbers. Some direct you to a Web page crafted to look exactly like a legitimate site, this helps the credibility issue along. And in this case, the victims are not necessarily stupid people — many intelligent, educated, cautious people have been taken in by this class of scam, simply because they weren't sufficiently skeptical or paranoid.
It requires a certain, perverse kind of alertness and discipline to survive the modern Internet, and being taken in by the cleverer scams is not necessarily an indictment of one's intelligence. I'd like to prove this to you with an example (please do not read ahead, that would spoil it). Here goes:
- On May first, you receive a letter from a financial advisor who wants your business. He makes a remarkable claim — he says he will correctly predict the direction of the Dow-Jones average for the next six months. He says you will receive a letter at the beginning of each month, and it will accurately predict whether the DJIA will rise or fall in the subsequent month. He wants your business, and he has decided to prove his value to you by making this run of predictions.
- For six months straight, to your shock, the financial wizard correctly predicts the direction of the Dow-Jones average for the following month. He is never wrong, and his mail arrives at such a time that you realize you could have acted on his advice and made a real killing in equities.
- On October first, the wizard makes his final prediction and points out — correctly — that he has never been wrong, and that you could have gotten way ahead of the average investor by following his advice.
- You sit in shock, looking at the letter. The wizard really did predict the market for six months straight. You really would have made a lot of money by acting on his predictions. He must be for real.
In fact, as convincing as this might be, it's a scam. To uncover how this scam works, being able to think is not enough. One must think in a different way — more skeptical and suspicious than most people are. Here is how this well-known scam works:
- The "wizard" acquires a big collection of addresses (e-mail, conventional, doesn't matter), the bigger the better.
- Each month, the "wizard" splits the list of addresses in two and mails a different message to each group. To group A, he says the market will rise. To group B, he says it will fall.
- At the end of the month, the wizard discards the addresses that got an incorrect prediction, splits the remaining addresses in two, and mails another prediction as in step 2 above.
- At the end of six months, the "wizard" has a list of prospects, each of which has received a seemingly miraculous run of correct market predictions. These are hot prospects and some of them are going to beg the "wizard" to take their money.
Now that you've read the explanation, I should add that there are any number of similar scams, scams that rely on the credulousness and basic honesty of the average person. Now think — if you had received the six amazing letters, what would you have done? Would you have been skeptical and guarded enough to see through it?
Remedies
I know I've made the spam problem seem rather hopeless, but there are ways to deal with it. I would suggest that people stop responding to spam mails, but confronting human stupidity is a losing proposition, so that's off the list. As in all modern political activity, whatever remedies are considered, they must work around the problem of stupid people.
One approach is to completely lock up the e-mail system. Throw out the present protocol and replace it with one that requires rigorous personal identification before a message even gets into the system. Most serious proposals represent a variation on this theme.
One such scheme is called "Trusted Sender". It relies on, among other things, specially formatted messages, a coöperative relationship between senders and recipients, and it can use existing e-mail communication channels. There is an open-source version called "Trusted E-mail Open Standard" that has produced a lot of discussion but little field use.
With regard to spam and various other illegal, exploitative activities, the bottom line is that to stop it, people will have to accept a closed, protected Internet. Because of the Internet's increasing importance to commerce and banking, it seems inevitable that this will happen, despite a lot of public resistance.
One intermediate solution is to change how e-mails are created and delivered. On this site, rather than publish an e-mail address as in years past, I've created a
message board that requires the user to read a code word from a graphic image and type it into a text entry form as part of the validation process. This strategy, called "captcha", is a way to assure that a human being is filling out the form (a computer could in principle read the characters from the graphic, but this is difficult).
This "captcha" strategy is only a stopgap measure, because as time passes there are more people that (apart from owning a computer) are in desperate financial straits and are willing to manually fill out "captcha" forms and post spam manually.
Here is a short history of my e-mail strategies — I think it's fairly typical. At first, I simply posted my e-mail address, also I had a guest book page, with publicly displayed entries that any visitor could create. Pretty soon spammers began abusing the guestbook, so I reluctantly shut it down, but I still posted my e-mail address.
Then the era of e-mail scanners arrived — robots that prowled the Internet looking for e-mail addresses. At that point I decided to create the first version of the message board, which has the advantage that no e-mail address is revealed and the user must manually type in the message — or so I thought. Pretty soon I realized people were using various kinds of programs and scripts to automatically fill out the form, so it became an open target to spammers.
I finally created the present message board with the "captcha" feature, and, as I said, this is only a stopgap measure. It will eventually fail to stop the tide of spam.
Legal Issues
First, I am not a lawyer. Now that we've dispensed with the formalities, if someone offends you, and if there is a remedy in law, and you both live on the same street, then there might be a point to legal action. If the two parties don't live on the same street, things become more complicated, and the greater the separation between the two parties, the greater the complexity.
There have been few noteworthy legal actions around the issue of spam. Many state-level laws have been passed, some eventually declared unconstitutional, some languishing in obscurity, untested in courts of law. But over the years spam has become much more of an international problem, and even though the sheer volume of spam has increased greatly, its sources have become more hidden (because of the use of botnets). So legal action has become less effective.
Another reason for the decreased effectiveness of legal action is the federal Can-Spam Act, which, while appearing to be a proactive step against spam, in practice legitimizes spam as well as undercutting most state anti-spam laws. In the U.S. legal system, when there is a federal law and a state law both of which address the same issue, the federal law nullifies the state law. As a result, passage of the Can-Spam Act wiped out a large number of state laws and replaced them with a rather weak law that permits more than it prohibits.
Before the Can-Spam Act, many states had declared spam illegal, period, and provided remedies in law for those who flouted the law. But the Can-Spam act only outlaws fraudulent spam, spam with a misleading subject line or a bogus reply address. In effect this means that spam that was once illegal is now legitimate, and at the federal level, which means states cannot contradict the "higher" law. Before Can-Spam, in some states people could sue spammers — Can-Spam takes away that right.
Among the Can-Spam Act's critics was ... get this ... the chairman of the FTC, the agency that until 2003 vigorously pursued and prosecuted spammers. Under the new law, this recourse is no longer available. And the National Association of Attorneys General, whose members are responsible for enforcing anti-spam laws, objected to the new law, saying in part "The bill creates so many loopholes, exceptions, and high standards of proof, that it provides minimal consumer protections and creates too many burdens for effective enforcement...We respectfully request that you not move forward...". But this and other protests were ignored.
Since Can-Spam went into effect and as predicted, spam has increased greatly, with a few show trials of egregious or incautious U.S. domestic spammers for the sake of appearances. In the meantime, spammers have used their new tools and power to bring down one anti-spam activist group after another. If a particular anti-spam service becomes effective enough to annoy the spammers, they launch a DDOS attack and persist until the anti-spam organization throws in the towel.
One example is the destruction of Blue Security, a computer security firm that would aggressively petition spammers to stop sending spam to its subscribers. In the Blue Security scheme, every time a subscriber received a spam e-mail, the spammer who sent it would automatically receive a reply demanding that the spam stop. The method was based on tit-for-tat, one message for one message, and the replies was persistent and immediate. This annoyed the spammers, apparently unaccustomed to receiving a taste of their own medicine, and they decided to take Blue Security out. And they did — they launched one DDOS attack after another until Blue security went permanently offline and dissolved itself.
The spammers are breaking the law, they are criminals, and they can destroy any business that annoys them. They can also hold legitimate businesses hostage for ransom, repeating DDOS attacks and crippling an online business until a specified amount of money is paid. In a recent series of attacks, blackmailers suspected of belonging to a Russian gang have demanded ransom in exchange for not bringing down various profitable online businesses. Most, but not all, of the targeted businesses have shown the good sense not to pay.
In a variation on the ransom theme, a hacker will attack a specific computer, cause all its important files to be compressed and encrypted, and all that is left at the end of the attack is a demand for payment (with an anonymous PayPal account number) to reveal the password that would allow the company to recover its encrypted files.
Conclusion
This article was meant to be a straightforward update to my previous anti-spam article, but has turned out to be more an analysis and summary of the activities of cybercriminals. It should make the reader aware that the Internet is entering a dangerous new phase in its evolution, one in which its vulnerabilities are being aggressively exploited by sophisticated, ruthless criminals.
Because of the increasing importance of the Internet to business and government, I believe it will have to be completely restructured, made less vulnerable than it is now. This will require a complete overhaul from top to bottom, from the design of packet protocols to how we establish our identities online.
The original Internet was designed to be as open and trusting as its original users. But those users are now in the minority, and a baser form of life has crawled out of the gutter and gotten hold of a computer. We all need to be on guard.
Feedback
 Share This Page
Share This Page
 Share This Page
Share This Page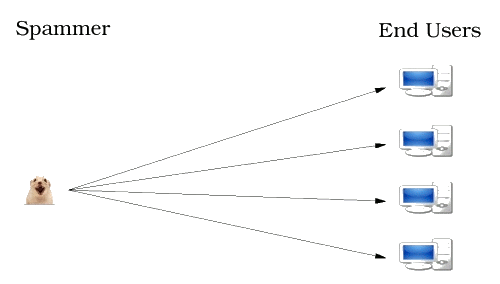

 Share This Page
Share This Page